Cryptography in Daily Life
We all are bored of our monotonous life and we wish to go for long vacations. CREATE AN ACCOUNT.
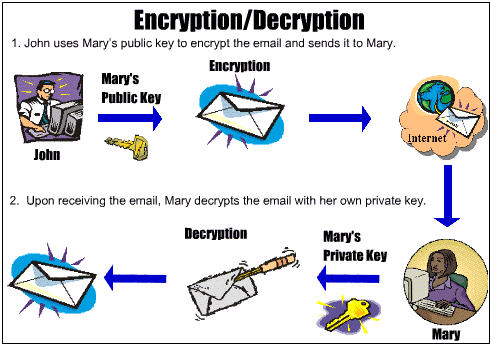
Real Life Applications Of Cryptography By Prashanth Reddy Medium
In earlier days video signals were not used to encrypt.
. Find Meetup events and groups so you can do more of what matters to you and meet people near you who share your interests. That is not reversible. A cryptocurrency is a digital or virtual currency that uses cryptography for security.
So far the Advanced Encryption Standard has achieved the targets placed during its inception. NortonLifeLock NortonLifelock Aug 5. Focus What you wont see covered The Daily Plan Coding Question Practice Coding Problems Lets Get Started Algorithmic complexity Big-O Asymptotic analysis Data Structures Arrays Linked Lists Stack Queue Hash table More Knowledge Binary search Bitwise operations Trees Trees - Notes Background Binary search trees.
If you do not wish to enter a password we will auto-generate one for you and send it to your email. BSTs Heap Priority Queue Binary Heap. When the AES Encryption algorithm succeeded the Data Encryption Standard as the global standard for encryption algorithms in 2001 it fixed many shortcomings of its predecessor.
Ultra was the designation adopted by British military intelligence in June 1941 for wartime signals intelligence obtained by breaking high-level encrypted enemy radio and teleprinter communications at the Government Code and Cypher School GCCS at Bletchley Park. In this study the characteristics of indoor PM25. 2FA on important accounts.
The Wild Life Protection Amendment Bill 2021 was taken up for consideration in Lok Sabha on Tuesday with the ruling BJP asserting that it would put India at the forefront of the battle to save the ecosystems of the world and the Opposition pushing for incorporating the suggestions of a parliamentary panel. As of yet little is known about the impact of different daily life behavior on PM25 diffusion and residents exposure in rural dwellings. In daily life she likes running and going to the amusement park with friends to play some exciting items.
A cryptocurrency is difficult to counterfeit because of this security feature. Norton 360 Deluxe - Winner Best. Conclusion By developing a greater understanding of the common encryption methods and cryptography algorithms in circulation today you will be better equipped to protect yourself from potential cyber attacks and breaches in data security.
Ultra eventually became the standard designation among the western Allies for all such intelligence. Cryptography is the study of secure communications techniques that allow only the sender and intended recipient of a message to view its contents. Technology is a constant in our daily lives but how much do we really understand it.
Minister of Environment Forest and Climate Change. Anyone with a satellite dish was able to watch videos which resulted in the loss for satellite owners so they started encrypting the. We need to prepare the budget for the trip the number of days the destinations hotels adjusting our other work accordingly and many more.
So as you go through your daily life be mindful of this reality and realize that More Secure doesnt mean Totally secure. Use of Matrices in Cryptography. The latest Lifestyle Daily Life news tips opinion and advice from The Sydney Morning Herald covering life and relationships beauty fashion health wellbeing.
That will make you smarter about your digital life. Feature Papers represent the most advanced research with significant potential for high impact in the field. Cryptography is a method to protect data and includes both encryption which is reversible and hashing which is one way.
It was seen as the future for encryption in daily life applications. WIN UP TO 200 IN FREE BITCOINS EVERY HOUR. Our doctors define difficult medical language in easy-to-understand explanations of over 19000 medical terms.
Back in 2016 the agency helped get the ball rolling on post-quantum cryptography by launching a process for soliciting the algorithms needed to do the job. Cryptography is the technique to encrypt data so that only the relevant person can get the data and relate information. Here comes the role of the maths.
Cryptography based on industry-tested and accepted algorithms along with key lengths that provide a minimum of 112-bits of effective key strength and proper key-management practices. She is also good at writing articles about computer knowledge and computer issues. The term is derived from the Greek word kryptos.
The highest concentration of PM25 in cold rural dwellings of Northeast China is often generated by using mini stoves for cooking and heating which can directly influence human health. BITCOIN SAVINGS ACCOUNT WITH DAILY INTEREST 50 REFERRAL COMMISSIONS FOR LIFE. Feature Papers are submitted upon individual invitation or recommendation by the scientific editors and undergo peer review prior to publication.
For this we have to plan things accordingly. Join us for 5-Factor Authentication- a podcast hosted by. Simultaneously the platform re-signs all packages with the ECDSA elliptic curve cryptography algorithm and uses HSM for key management further bolstering security.
We can thank the efforts of cryptography specialists working in tandem with the National Institute of Standards and Technology for helping the industry prepare for this threat. She specializes in writing articles about backing up data systems cloning disks and syncing files etc.

5 Applications Of Cryptography In Daily Life Ronanthewriter
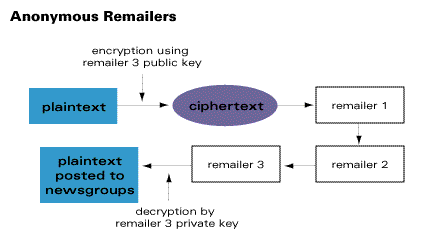
Real Life Applications Of Cryptography By Prashanth Reddy Medium
Comments
Post a Comment